Communication is difficult, also when it comes to the risk of cyberattacks. The board and management need a clear basis for decision-making, but the communication needs to improve because it is often too technical or too high-level and abstract. Both cases are useless for a meaningful discussion and as a basis for decisions.
Risk matrices and traffic lights are examples of high-level and abstract communication. Although they are widespread tools, they should not be used as a basis for decision-making of any importance. As we have addressed in previous posts, they may create a false sense of security.
Excessive technical communication disturbs decision-making. Although the intention is good, it overflows the board and management with unnecessary details, which reduces the overview and makes actions difficult. It is like receiving a report from the local workshop stating that the timing belt in your car has been replaced while you are trying to steer the car on an icy road. Not relevant.
FACTS BEFORE FEELINGS
Ten years ago, cyberattacks did not get the attention they do now. The public exposure of incidents like the cyberattack on the Danish railway company DSB on October 29th 2022, is one example. One thing is attention; another is involvement. If the board and management are to be active partners in cyberattack mitigation, high-quality fact-based information is necessary.
First, the risk of cyberattacks must be expressed in a language everyone understands. We recommend you express loss in your local currency, e.g., DKK, and probability as a percentage per year. It enables you to compare areas of risk.
Some risk managers would probably object and argue that the recipients are satisfied with risk matrices and traffic lights. Yes, recognition evokes pleasure, but would that satisfaction be similar if presented with a quantitative alternative? The challenge probably resides closer to the people who produce the material. It takes effort to learn how to assess your company’s IT risks quantitatively, but it will be a solid and safe investment.
8 FUNDAMENTAL QUESTIONS FOR CYBER RISK MANAGEMENT
Once we have established that cyber is a real and serious threat, we need more nuance. Any kind of risk management must be able to answer the following questions:
- What is the overall level of cyber risk?
- What would a typical cyber incident against our company look like?
- What is the probability of a typical and an extreme cyberattack?
- How does our risk compare to other companies in our industry?
- How vulnerable are we to these cyberattacks?
- How much can an extreme cyberattack cost us?
- What is the cost and impact of cyber risk mitigation?
- Is cyber insurance worth it?
Cyberattacks: HOW DO WE REACT APPROPRIATELY?
Let’s look at how a good quantitative risk assessment can create a solid basis for decision-making for the board and management.
We assume a quantitative risk assessment has been carried out based on data from measurements, observations and calibrated experts. In this process, we have decomposed the loss of a cyber incident, which means that we now understand what happens in the company when one or more critical systems are unavailable, data is faulty, etc.
We recall that “all models are wrong, but some are useful”. Yet, we should strive to create a model that incorporates the knowledge of and learnings from cyber incidents, their courses, loss patterns and probabilities. This is, in fact, possible today.
Let’s look at six key figures that can answer the earlier-mentioned questions:
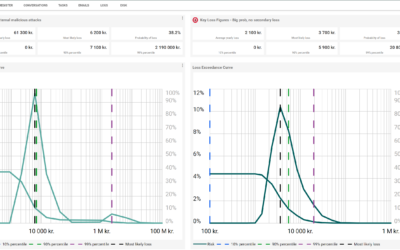
1. The expected annual loss in your currency
A key figure which describes the total average loss from all highlighted cyber scenarios. Both the frequent ones with small losses and the rare ones with severe losses. If you put this amount aside annually, over a period, you would be able to cover your future losses or be able to insure yourself.
2. The expected annual loss in your currency per area
Here we get an understanding of different risk areas juxtaposed with each other. With the probability factored in, we can now see the areas (cyber, internal mistakes, outsourcing, compliance and physical incidents) in relation to each other. If we, e.g., lose an amount annually on outsourcing that corresponds to the contract sum, our choice of supplier may be relevant to discuss.
3. The most likely loss in case of a cyber incident
When assessing losses quantitatively, we see where the loss distribution peaks. In other words, the loss that is most likely in the event of a cyber incident. When we talk about cyber incidents, we remember the most extreme incidents (e.g., NotPetya in Maersk 2017), but the truth is that several incidents do not cause extreme losses. In these cases, the company experiences downtime and lost data, but it won’t be extremely expensive. This key figure can describe these less impactful cases.
4. The likelihood of cyber incidents
A key figure in percentage per year. You will typically communicate an overall probability of being hit by a cyberattack, regardless of its loss size, and divide the probability into event types from different attack types.
5. The probability of a loss greater than [INSERT VALUE]
Many boards’ only reference to cyberattacks is the stories from the three most significant incidents in history. How grim it could turn out in our organization is a relevant figure to know. The key figure can, e.g., read: “The probability that a cyberattack costs us more than DKK 30.000.000 is 0.5%”.
6. The 99% fractile for a cyber-attack
Similar to the point above, but based on probability, this figure underlines how expensive a potential cyberattack can become. To reiterate, the 99% fractile means there is only a 1% probability that loss from a cyberattack will be higher than the key figure. The number you will uncover is high, but having seen and reflected on this may result in some peace of mind for you and the board as the number is no longer utterly unknown to you.
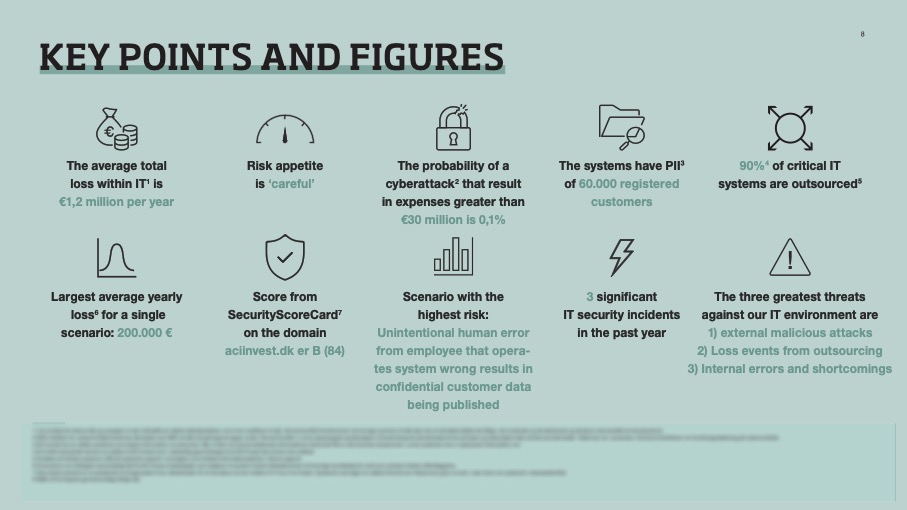
A good quantitative risk assessment can generate many other valuable key figures. Below is an example from an overview used in a boardroom.
COMMUNICATe AND REDUCE
It is a good idea to discuss what is expected of information, just as one should be trained in consuming this information. If you make that effort, you will find that you get top management and a board of directors who are not only aware of the cyber risk but also get involved in cyber risk.
It is uplifting when we have faced potential cyberattacks together and, e.g., understand how costly a loss we can realistically suffer from a severe cyberattack. Together, we are now able to articulate and process cyber risk, leading to data-supported decision-making that ultimately reduces risk.
Enjoy your zealous work providing key tactical and strategic information about cyber risk to management and the board of directors.