Thursday, December 7, 2023 was an important day for ACI.We held our December seminar on IT Risk quantification.We were proud that more than 180 people had signed up for the seminar from more than 100 organizations across Europe.We shared experiences from 5 years of...
Knowledge
Part Two: ‘We Should Never Have Said That’ and How to Avoid It Being Used Against You Before It’s Too Late
Earlier this year, the first part of this article was published. It’s a good place to start to learn why you want to understand your company’s attack surface. Websites and online databases tend to over-share – you should aim to limit this. But some...
Ask fewer and better questions – Right now!
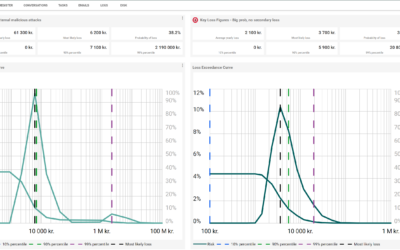
In a previous article, When a robot gives better estimates than a human, Bo Thygesen from ACI describes how we use the LENS model to avoid human bias and have a “robot” estimate probability and loss for hundreds of systems better and faster than a human can do. How...
Webinar: An introduction to quantitative methods for cyber risk management
Almost daily, we hear about how cyber threats and IT risks increase globally across industries. Sadly, the methods and tools used for IT risk management today do not deliver the consistent decision support that organizations need. On March 23rd 2023, we conducted a...
ISO 27005 – What is it and how Is it Wrong About Quantitative Risk
The International Standards Organization recently published an updated version of their guidance for information security risk management, but they have missed the mark entirely on quantitative methods. What is ISO 27005? The ISO/IEC-27005 is one of the key standards...
What are information assets & how to Identify them in 5 steps?
An important step in any IT risk management process is to clearly define the information assets in scope. But what is an information asset really? How can you best describe your important information assets? And why is it so important to spend time on establishing a...
What’s the fun in that?
The last couple of years have reminded us of how dangerous and fluid the world is. It's become our new normal. War in Europe, climate changes, macroeconomic problems and cyber attacks are just some of our society's issues. Now, in Denmark, we talk a lot about...
‘We should never have said that’ and how to avoid it being used against you before it’s too late
‘Loose Lips Sink Ships’ was printed on a propaganda poster during World War 2. It was one of the key messages from the ‘United States Office of War Information’, which urged citizens to avoid careless chatter that could potentially undermine war activities. The same...
Give me a number!
People are often asked about estimates in investments, the opening of new business areas, projects and budgeting. The estimates given are subject to uncertainty. No one can tell the exact amount, time etc., that will occur in the future. Despite this...
The simplest risk metrics that we just can’t agree on
Inherent risk… residual risk… current risk? When your risk manager or regulatory affairs asks about your “inherent risk”, it highlights a fundamental flaw in qualitative risk assessments. Here’s why - and how to fix it. Although most of us engage in some form of risk...